Phishing Scams
Learn how to recognize and avoid phishing attempts that try to steal your personal information.

What is Phishing?
Phishing is a type of scam where criminals pose as trustworthy organizations to trick you into revealing personal information.
The term "phishing" comes from the idea that scammers are "fishing" for your private information. They send deceptive messages that appear to come from legitimate sources like your bank, the government, or businesses you trust.
Their goal is to steal sensitive information such as:
- Usernames and passwords
- Credit card numbers
- Social Security numbers
- Banking information
- Personal details that can be used for identity theft
Common Types of Phishing
Phishing attempts can come in many forms. Here are the most common types you should be aware of:
Email Phishing
The most common type, where scammers send fake emails that appear to be from legitimate companies or organizations.
They often claim there's a problem with your account or an attractive offer, and include links to fake websites.
Spear Phishing
A more targeted approach where scammers use personal information they already know about you to make their messages more convincing.
These attacks are personalized and may mention your name, location, or recent purchases.
Smishing (SMS Phishing)
Phishing attempts sent via text message. They often claim to be from your bank, delivery services, or government agencies.
These texts typically contain urgent messages and suspicious links to click.
Vishing (Voice Phishing)
Phone calls from scammers pretending to be from legitimate organizations. They often create a sense of urgency or fear to get you to share information.
Common examples include fake calls from "tech support," the IRS, or your bank.
Pharming
A sophisticated attack that redirects you to fake websites even when you type the correct web address into your browser.
These fake sites look identical to real ones but are designed to steal your login information.
Clone Phishing
Scammers create an exact copy of a legitimate email you've previously received, but replace the links or attachments with malicious ones.
They often claim to be a "resend" or "updated version" of the original message.
Organizations Commonly Impersonated in Phishing Scams
Scammers typically pose as trusted organizations. Be especially cautious of unexpected messages from these entities:
Banks
Email Providers
Online Stores
Government Agencies
Tech Companies
Delivery Services
Important to Remember
These organizations typically will NOT:
- Send emails asking for passwords or account numbers
- Request personal information via email or text
- Send attachments you weren't expecting
- Create urgency with threats of account closure
- Send links asking you to log in (instead of directing you to type their web address directly)
How to Spot Phishing Attempts
Here are the warning signs that can help you identify phishing:
Email Phishing Red Flags
Suspicious Sender Address
Look carefully at the sender's email address. It might look similar to a legitimate company but have small differences.
Example: amazon-support@secure-notice.com instead of support@amazon.com
Generic Greeting
Legitimate companies typically use your name. Be suspicious of "Dear Customer" or "Dear Account Holder."
Urgent Action Required
Scammers create a sense of urgency to make you act without thinking.
Example: "Your account will be suspended in 24 hours if you don't verify your information"
Poor Grammar and Spelling
Many phishing emails contain obvious spelling mistakes or awkward phrasing that legitimate companies would catch.
More Warning Signs
Suspicious Links
Hover your mouse over links (without clicking) to see where they really lead. The URL shown might be different from where the link actually goes.
Requests for Personal Information
Legitimate organizations rarely request sensitive information like passwords or account numbers via email or text.
Unexpected Attachments
Be wary of unexpected email attachments, even if they appear to come from someone you know.
Too Good To Be True
Offers that seem unusually generous, like prizes, giveaways, or incredible deals are often phishing attempts.
Phishing Email Example: Spot the Warning Signs
Let's analyze a typical phishing email to see the warning signs in action:
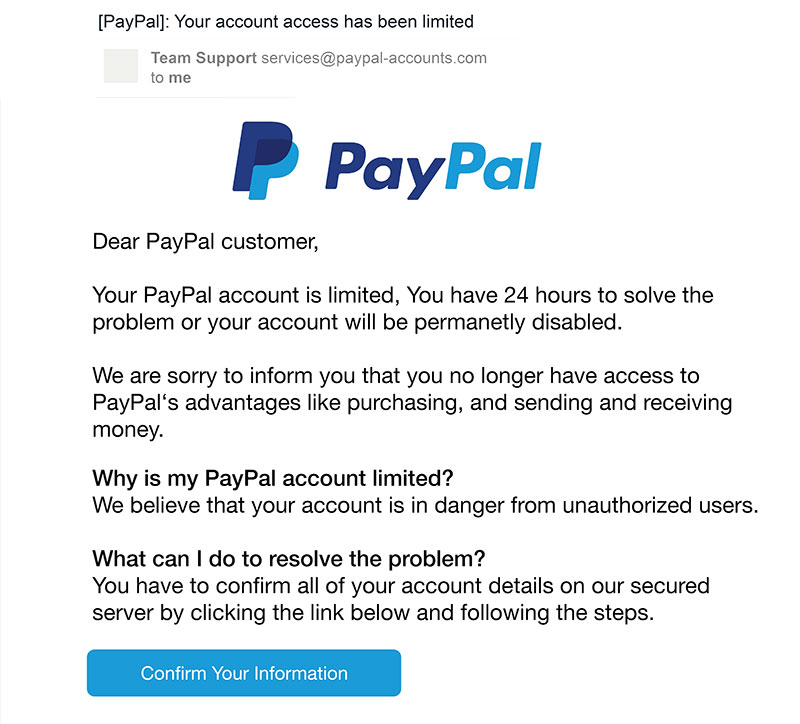
Warning Signs in This Email
Suspicious Sender
The email appears to be from Paypal, but the actual sender address is services@paypal-accounts.com, not an official paypal.com domain.
Generic Greeting
"Dear Paypal Customer" instead of using your actual name. Amazon would normally address you by name if you have an account.
Urgent Language
"account is limited" and "You have 24 hours" create a false sense of urgency to make you act without thinking.
Suspicious Link
The "COnfirm Your Information" button likely leads to a fake website designed to steal your login information.
Grammar Errors
Notice the awkward phrasing and minor grammar mistakes that a large company like Paypal would not make.
How to Protect Yourself from Phishing
Follow these practices to safeguard your personal information:
Never Click Suspicious Links
Instead of clicking links in emails, type the website address directly into your browser or use your saved bookmarks.
Verify the Sender
Check email addresses carefully. Look beyond the display name to see the actual email address.
Keep Personal Information Private
Never share passwords, account numbers, or Social Security numbers in response to an email or call you didn't initiate.
Call to Verify
If you receive a suspicious message claiming to be from a company, call them directly using the phone number from their official website—not the number in the message.
Be Skeptical of Urgency
Legitimate organizations rarely demand immediate action. Take time to verify communications before responding.
Use Security Software
Keep your computer and devices protected with up-to-date security software that can help identify and block phishing attempts.
Remember This Rule
When in doubt, don't click, reply, or call back. Verify through official channels instead.
What to Do If You Suspect Phishing
If you receive a suspicious message or think you may have encountered phishing:
For Email Phishing
- Don't click any links or download any attachments
- Don't reply to the sender
- Forward the email to:
- The Anti-Phishing Working Group: reportphishing@apwg.org
- The FTC: reportfraud@ftc.gov
- The organization being impersonated (use their official contact information, not what's in the email)
- Delete the email from your inbox
For Text Message Phishing
- Don't click any links in the message
- Don't reply to the message
- Forward the message to 7726 (SPAM) to report it to your wireless carrier
- Delete the message
For Phone Call Phishing
- Don't provide any personal information
- Hang up immediately
- If the caller claimed to be from a company or agency you deal with, call them directly using their official number (not the number that called you)
- Report the call to the FTC at reportfraud.ftc.gov
For Website Phishing
- Close the website immediately
- Run a security scan on your device
- If you entered any information, contact the real organization immediately
- Report the website to Google at safebrowsing.google.com/safebrowsing/report_phish/
If You've Already Responded to a Phishing Attempt
If you've already clicked a link, downloaded an attachment, or shared information with a suspected phishing scam:
- Change your passwords immediately for any accounts that may be affected
- Contact your bank or credit card companies if you shared financial information
- Monitor your accounts closely for suspicious activity
- Consider placing a fraud alert on your credit reports
- Report identity theft at identitytheft.gov if your personal information was compromised
Need immediate help? Visit our I've Been Scammed page for detailed recovery steps.
Real-World Phishing Examples
Here are some common phishing scenarios to be aware of:
Why Seniors Are Targeted by Phishing Scams
Scammers often specifically target older adults for several reasons:
Why Scammers Target Seniors
- Financial Resources: Many seniors have retirement savings, home equity, or good credit that scammers want to access
- Less Tech Experience: Some older adults may be less familiar with digital security practices
- Politeness: Many seniors were raised to be courteous and may find it difficult to hang up on someone or say "no"
- Trust: Older generations often grew up in an era with less fraud, making them more trusting of official-looking communications
- Living Alone: Many seniors live alone and don't have someone nearby to consult about suspicious messages
Special Phishing Tactics Used Against Seniors
- Medicare/Health Insurance Phishing: Emails or calls claiming to be from Medicare requiring "verification" of information
- Social Security Scams: Messages claiming there's a problem with your Social Security benefits requiring immediate attention
- Retirement Account Phishing: Emails appearing to be from investment companies managing retirement funds
- Family Emergency Scams: Messages claiming to be from grandchildren or other relatives in trouble
- Charity Scams: Phishing that appeals to seniors' generosity by impersonating charitable organizations
Remember:
Being targeted by scammers is not a reflection of intelligence or capability. These are sophisticated criminals who use psychological tactics and deception against everyone. The best defense is awareness and caution.
Helping Others Stay Safe from Phishing
Share your knowledge to protect family and friends:
For Family Members
- Share this information with family members who might be vulnerable
- Offer to be a "verification buddy" who can be called when suspicious messages are received
- Help set up security features on their devices
- Create a family password that only family members would know (to verify identity in emergencies)
For Your Community
- Share phishing alerts with friends and neighbors
- Organize an information session at your local community center
- Print and share our phishing prevention guide
- Report local phishing scams to community bulletins
For Yourself
- Stay informed about new phishing tactics by checking our Scam Alerts page
- Practice identifying phishing with our interactive simulator
- Consider setting up a dedicated email address for online accounts
- Sign up for our scam alert notifications
Advanced Protection Methods
Consider these additional steps for stronger protection against phishing:
Technical Safeguards
- Two-Factor Authentication (2FA): Set this up on your important accounts so even if scammers get your password, they can't access your account
- Password Manager: Use a secure password manager to create and store strong, unique passwords for each account
- Email Filtering: Set up strong spam filters on your email account
- Security Software: Keep anti-virus and anti-malware software up-to-date
- Browser Extensions: Consider security extensions that warn about malicious websites
Behavioral Safeguards
- Verify Independently: Always verify requests by contacting the organization directly through their official website or phone number
- Check the URL: Before entering any information on a website, check that the web address is correct and secure (https://)
- Create a Verification Protocol: Establish a personal system for verifying legitimate requests
- Stay Informed: Keep up with the latest phishing techniques
- Trust Your Instincts: If something feels suspicious, it probably is
Need Help Setting These Up?
If you need assistance implementing any of these security measures, consider:
- Asking a tech-savvy family member or friend for help
- Taking a computer security class at your local library or senior center
- Hiring a reputable computer technician for a one-time security setup
Think You've Encountered a Phishing Attempt?
If you're unsure about a message or think you may have fallen victim to phishing, we're here to help.